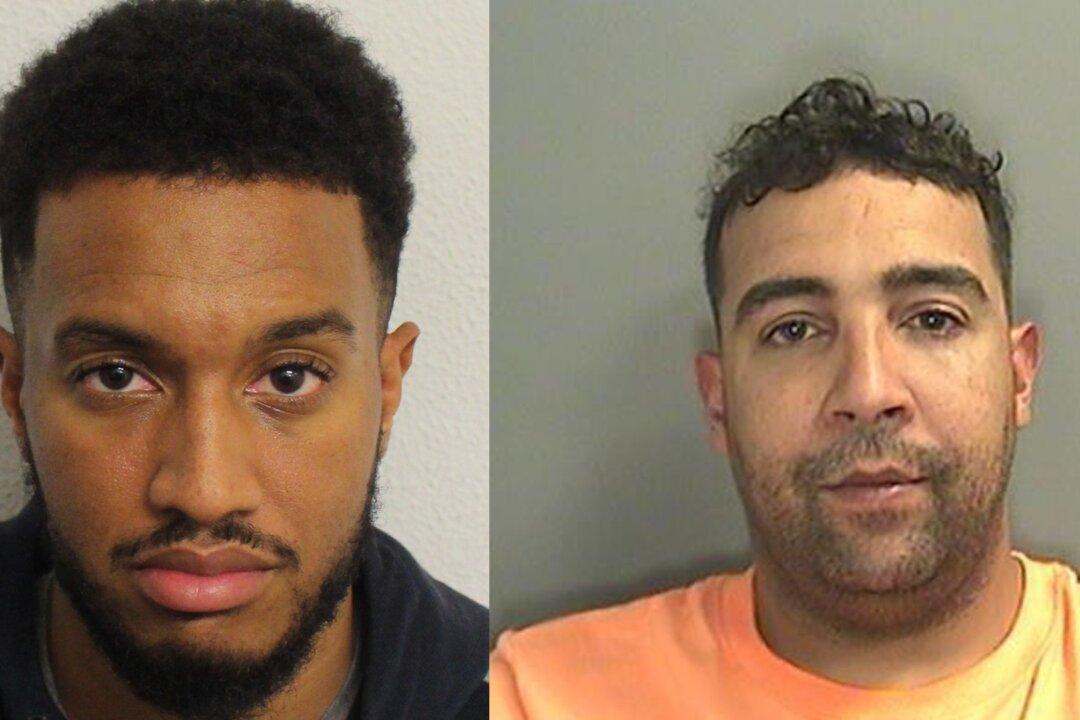
LONDON—Two British men have been jailed for conspiracy to murder and a number of other crimes after a prosecution that was made possible only when French police hacked into the EncroChat network.
Paul Fontaine, 36, from Hackney, east London, and Frankie Sinclair, 34, from Cardiff, Wales, were jailed for life, with a minimum term of 18 years, on Friday for conspiracy to murder after a trial at the Old Bailey in London.