News Analysis
For more than a decade, cybersecurity experts across the government and private sectors have sounded the alarm about the increasing risks posed by technology products manufactured in China.
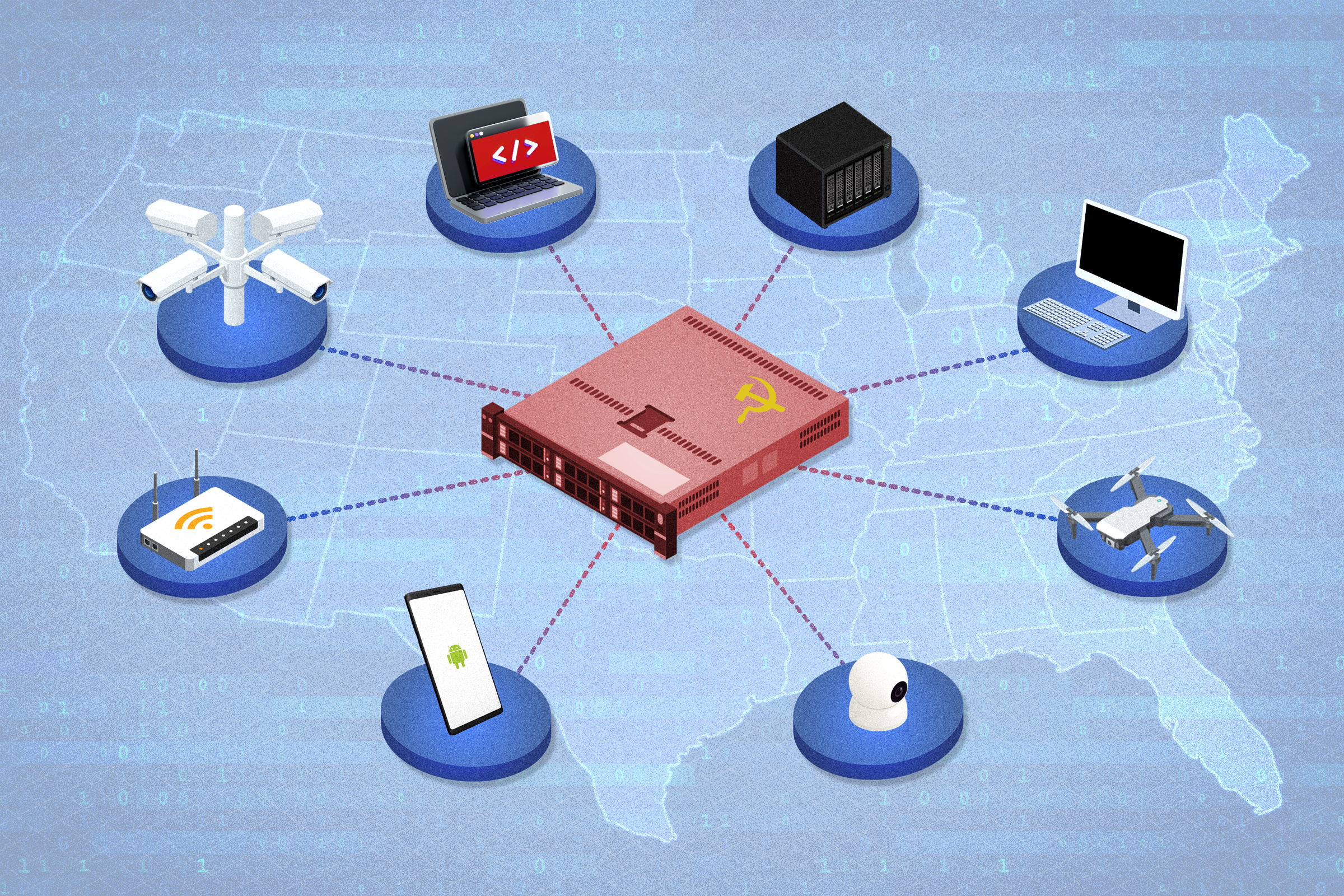
For more than a decade, cybersecurity experts across the government and private sectors have sounded the alarm about the increasing risks posed by technology products manufactured in China.